Hello everyone! I am a entering into cybersecurity and just cracked my first challenge on the Hackthebox platform. Today, I'm sharing my experience tackling one of the "Starting Point" machines called "Meow". My aim is to work through each starting point machine and to write writeups along the way.
You can find all the machines from starting point module from here
Upon connecting to the target machine via OpenVPN, HackTheBox promptly provided me with the IP address.
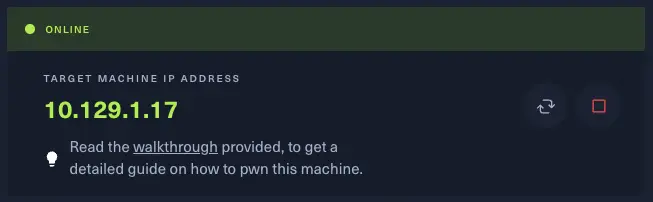
TARGET MACHINE IP ADDRESS
10.129.1.17
Let’s get started with the machine now by scanning the IP address on our local machine using Nmap.
nmap 10.129.1.17 -Pn
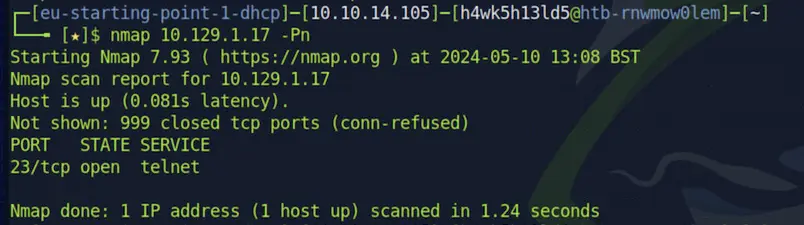
-Pn indicates to Nmap that it should not perform host discovery and should treat the target as online, regardless of its actual state.
As we can see there is an open port 23/tcp and the service running is 'telnet'. I immediately searched online to learn more about telnet and I found that TELNET is commonly used by terminal emulation programs that allow you to log into a remote host. It's crucial to note that telnet can be a potential security vulnerability due to factors like anonymous login options, misconfigurations, and weak passwords. I decided to explore this further by attempting to log in via telnet using the following command:
telnet 10.129.1.17
And we are greeted to the service like this:
Upon being prompted to log in, I decided to try "root" as the username, given that the challenge aims for obtaining the root flag. Surprisingly, the username "root" was accepted without requiring a password, granting me access to the target via telnet.
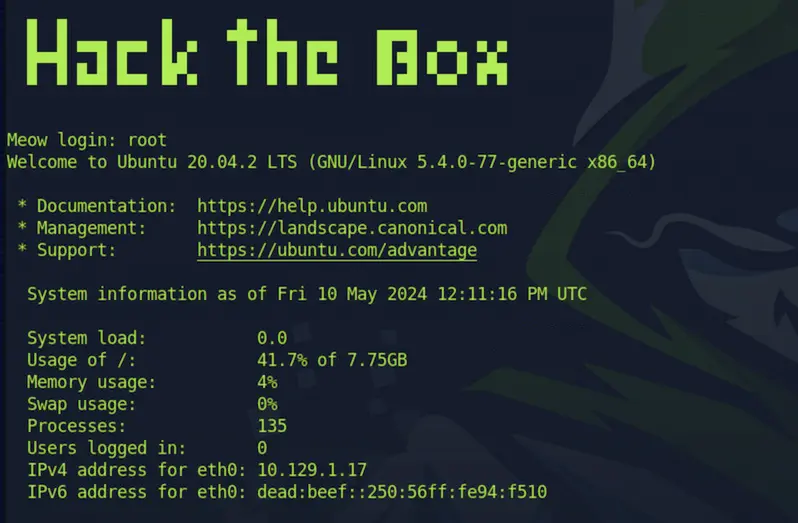
After executing the ls command, I discovered only two files present in the directory, one of which was named flag.txt.
It seemed remarkably straightforward, almost deceptively so. For beginners, this might indeed serve as an excellent starting point. With no further ado, I used the cat command to retrieve the contents of flag.txt, swiftly completing this stage and preparing to advance to the next challenge.
cat flag.txt
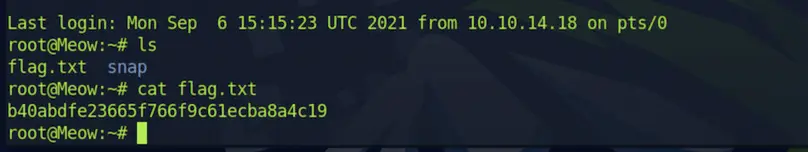
AND I GOT THE FLAG! ❤️~
Second part of the flag is: B3