OffSec - Bunyip Walkthrough
In this walkthrough, we’ll exploit an MD5 length extension vulnerability in a web application to gain initial access. From there, we’ll abuse sudo privileges on safe-backup by encrypting our own SSH key backup and swapping it in place of the /root SSH directory for decryption.
Enumeration
Nmap
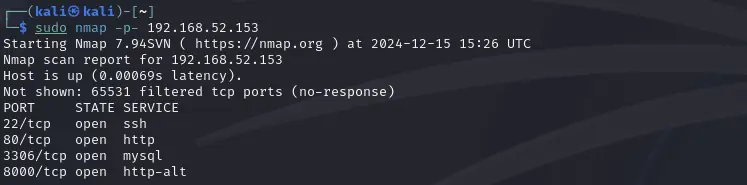
As always, We'll begin with an nmap scan.
kali@kali:~$ sudo nmap -p- 192.168.xx.xxx
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-02 00:39 EST
Nmap scan report for 192.168.83.136
Host is up (0.00067s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8000/tcp open http-alt
MAC Address: 00:0C:29:65:3E:10 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.36 seconds
Exploitation
MD5 Length Extension Attack
When we navigate to the website running on port 8000, we find a Node.js application that allows users to execute server-side code, but only if the code is properly signed. We’re given a valid signature for a simple “Hello World” code block. However, any modifications to this code trigger a ‘Signature Mismatch’ error, preventing execution.
Upon examining how the signature is generated, we suspect the app is vulnerable to an MD5 length extension attack. This attack works by taking a known hash (the provided signature) and reconstructing the internal state of the MD5 function. Once that state is known, we can extend the message (the code block) by adding new data while preserving a valid hash.
The following Python script handles this for us: it takes the original code block and signature, calculates the necessary padding, appends our custom code, and submits it to the server for execution.