Walkthrough of vmdak
Introduction
Hello everyone! I'm back with another walkthrough. This time, I tackled "VMDak," an intermediate-level Linux box from OffSec Proving Grounds. This box offered a unique challenge, requiring a series of steps after gaining initial user access.
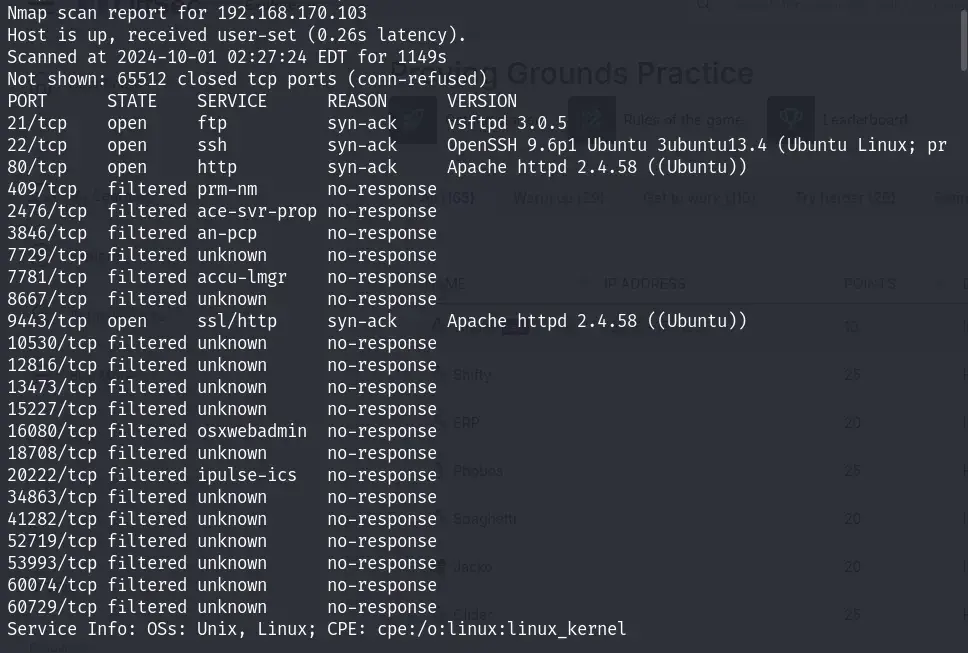
Let's jump into the hacking process. As always, we started with some initial reconnaissance, beginning with an Nmap scan. The scan revealed open ports: 21, 22, 80, and 9443, giving us multiple avenues to investigate further.
Port 21:
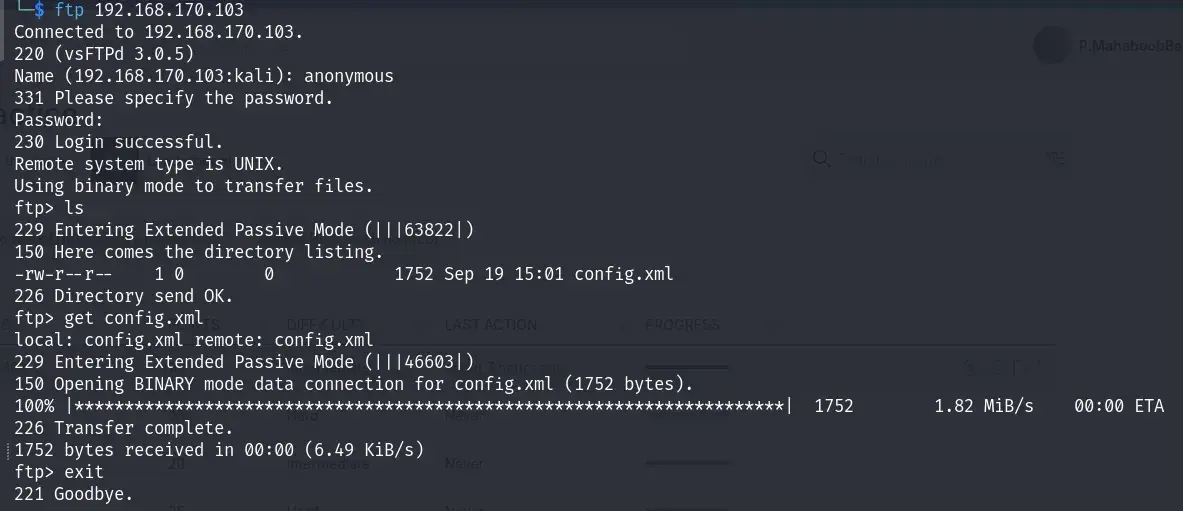
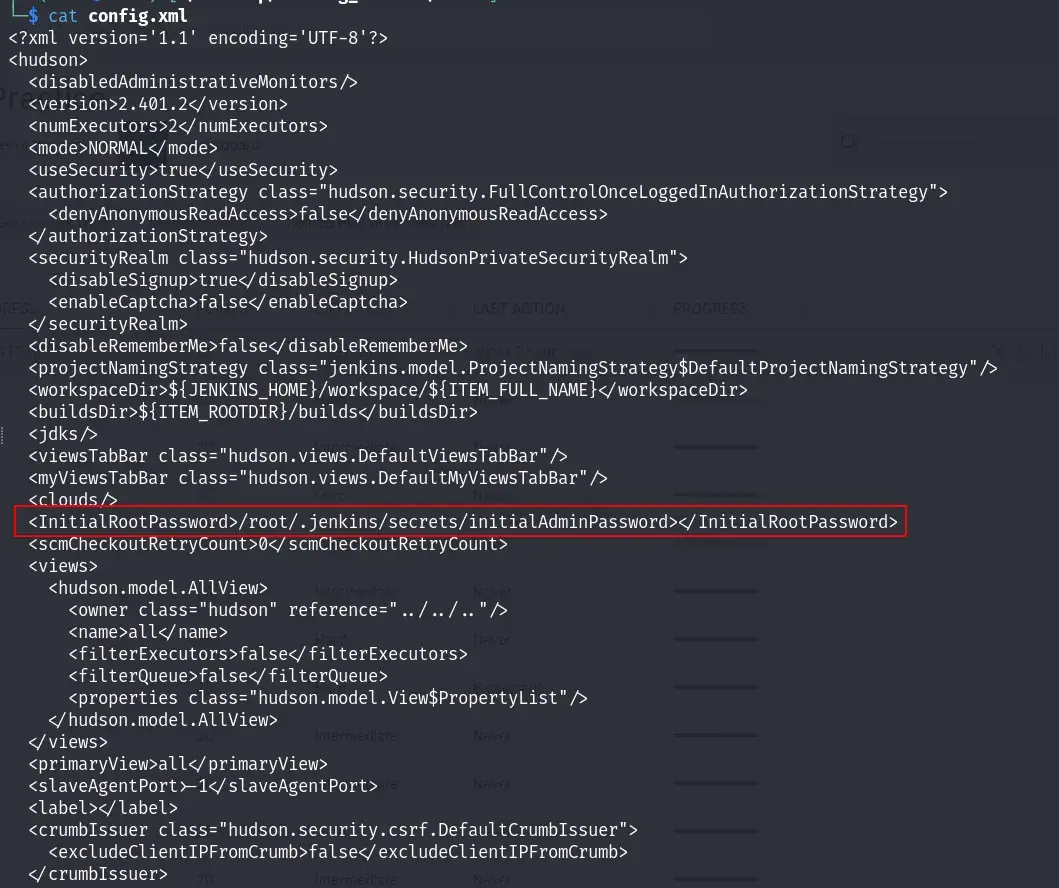
Starting with port 21, we tested anonymous login and successfully accessed the FTP server. While browsing the FTP directory, we found a file named config.xml, which we downloaded for further analysis.
Examining config.xml initially didn’t reveal anything notable, but it did indicate the path to the Jenkins initial admin password, a potentially valuable discovery.
Port 80:
Port 80 displayed the standard Apache2 welcome page with no additional information of interest.
Port 9443:
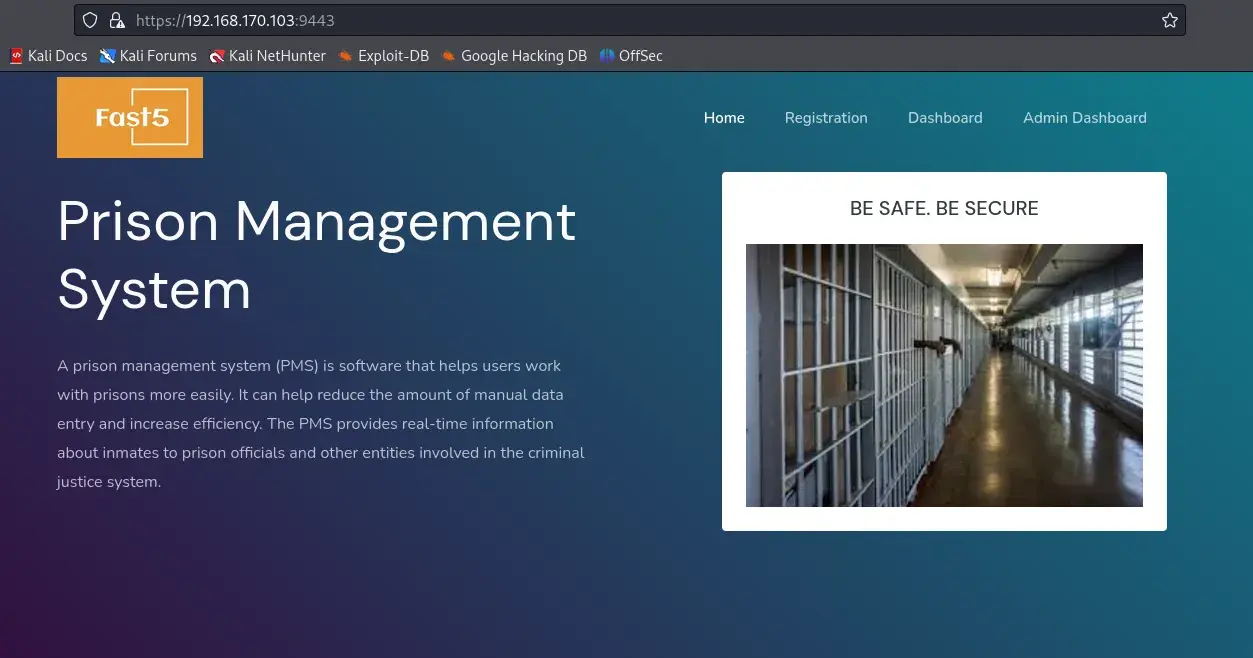
Moving on to port 9443, we found a web application—a prison management system. However, accessing the Admin dashboard redirected us to a login page.
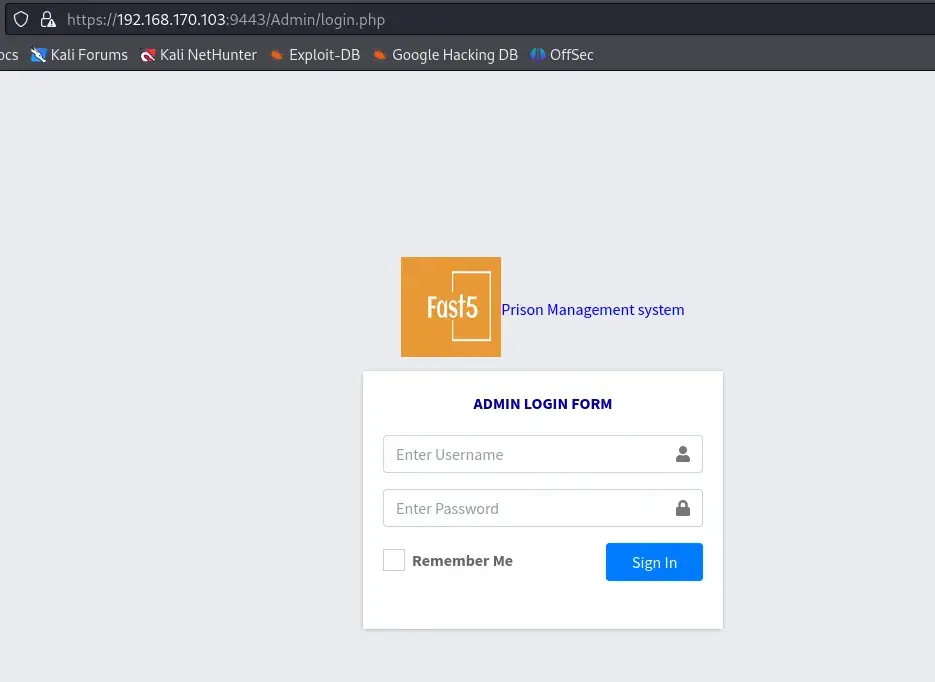
Upon researching vulnerabilities for this system, we identified a known SQL injection vulnerability in its login page.
Reference: OffSec's Exploit Database Archive
Vulnerability: Prison Management System - SQL Injection Authentication Bypass
Using this SQL injection technique, we bypassed authentication and successfully logged into the application.